Solutions
Control your risk with confidence
The Synapse-RM Tool is a comprehensive risk management module within a larger application designed to help organizations identify, assess, and manage cybersecurity risks effectively. It enables organizations to have a clear view of their risk posture, monitor third-party risks, and maintain compliance with relevant industry standards and regulations.
About the Platform
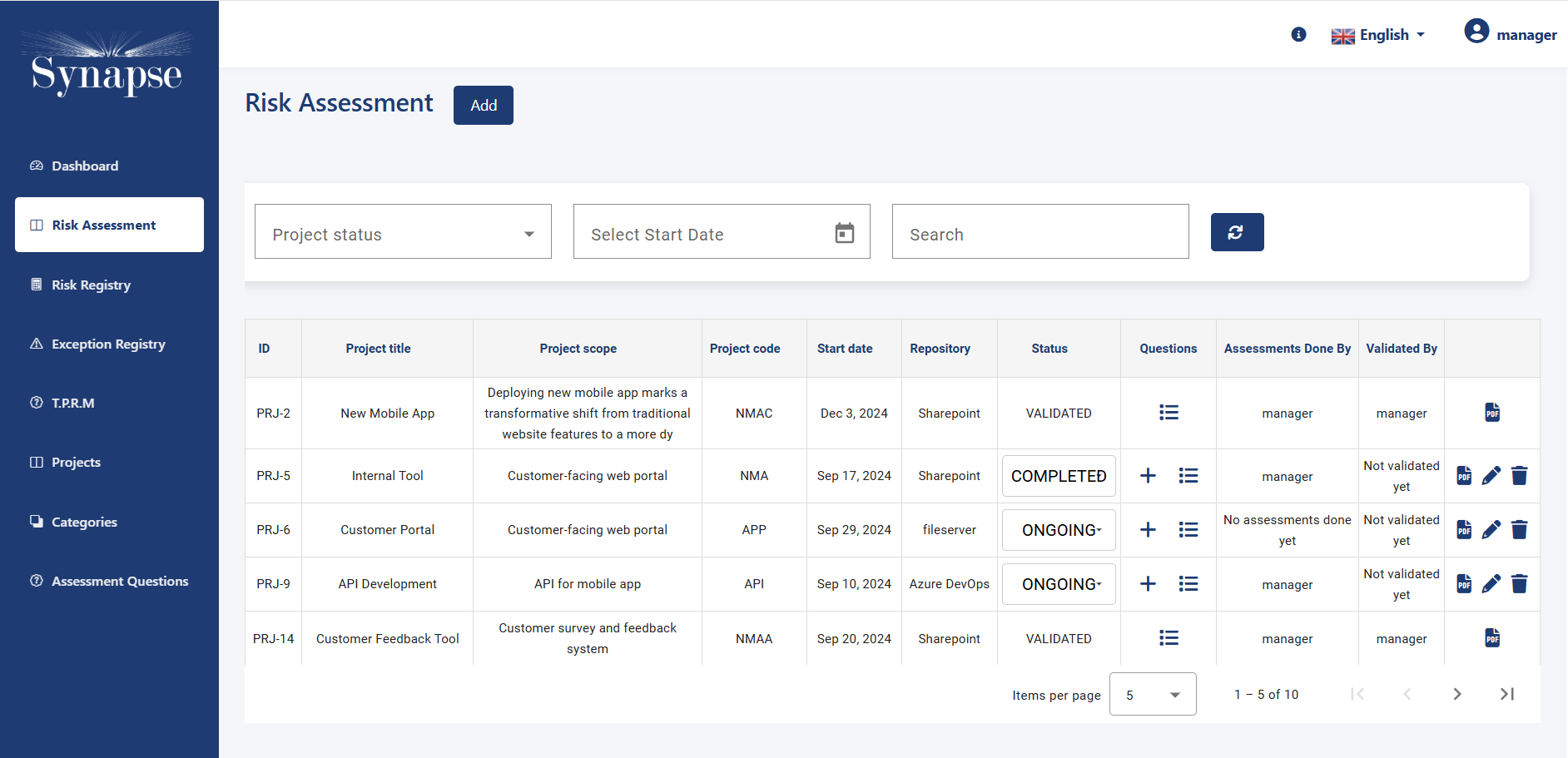
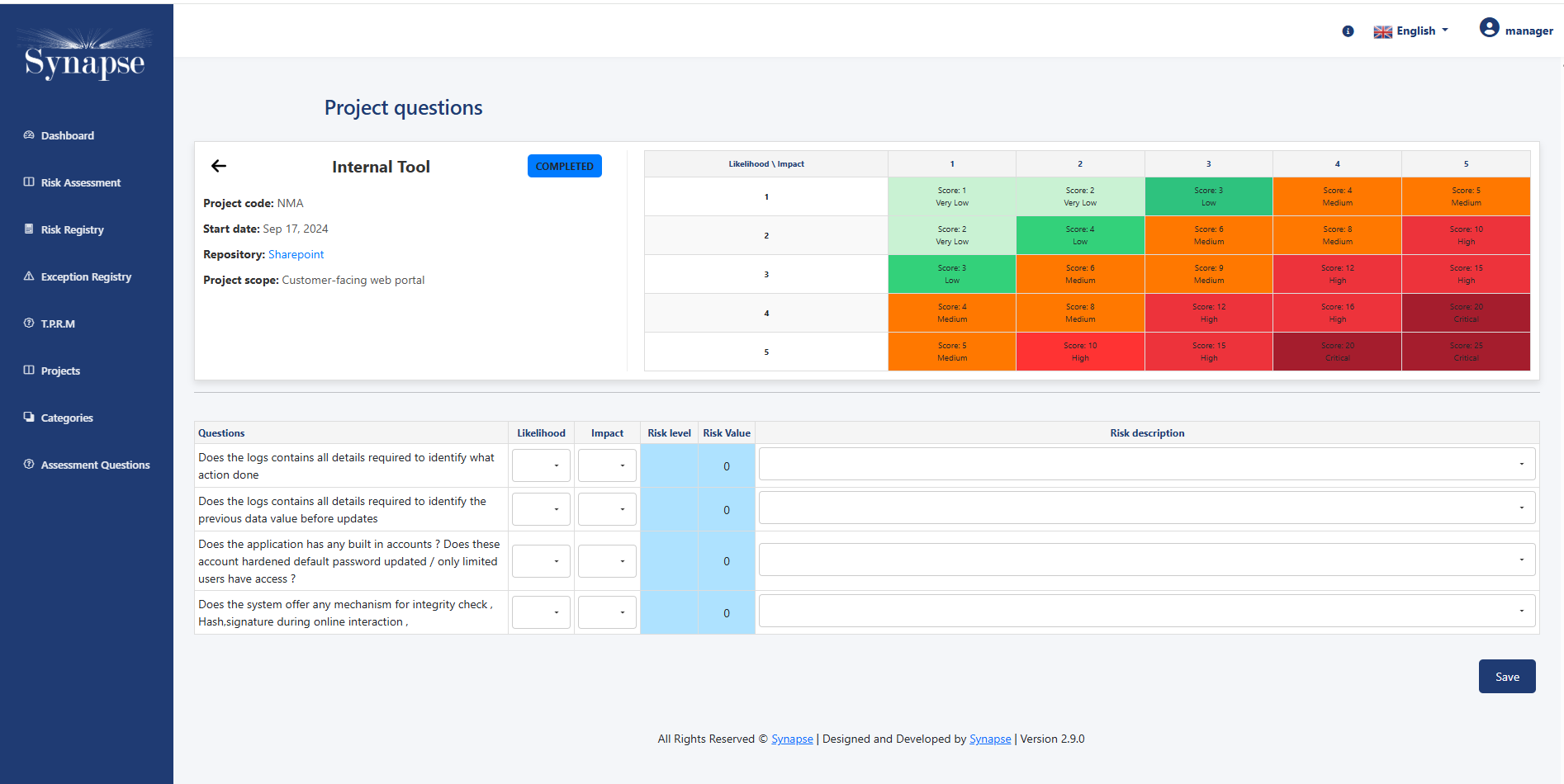
- Risk assessment based on security requirement
- Third Party Risk management
- 360° view to the CISO
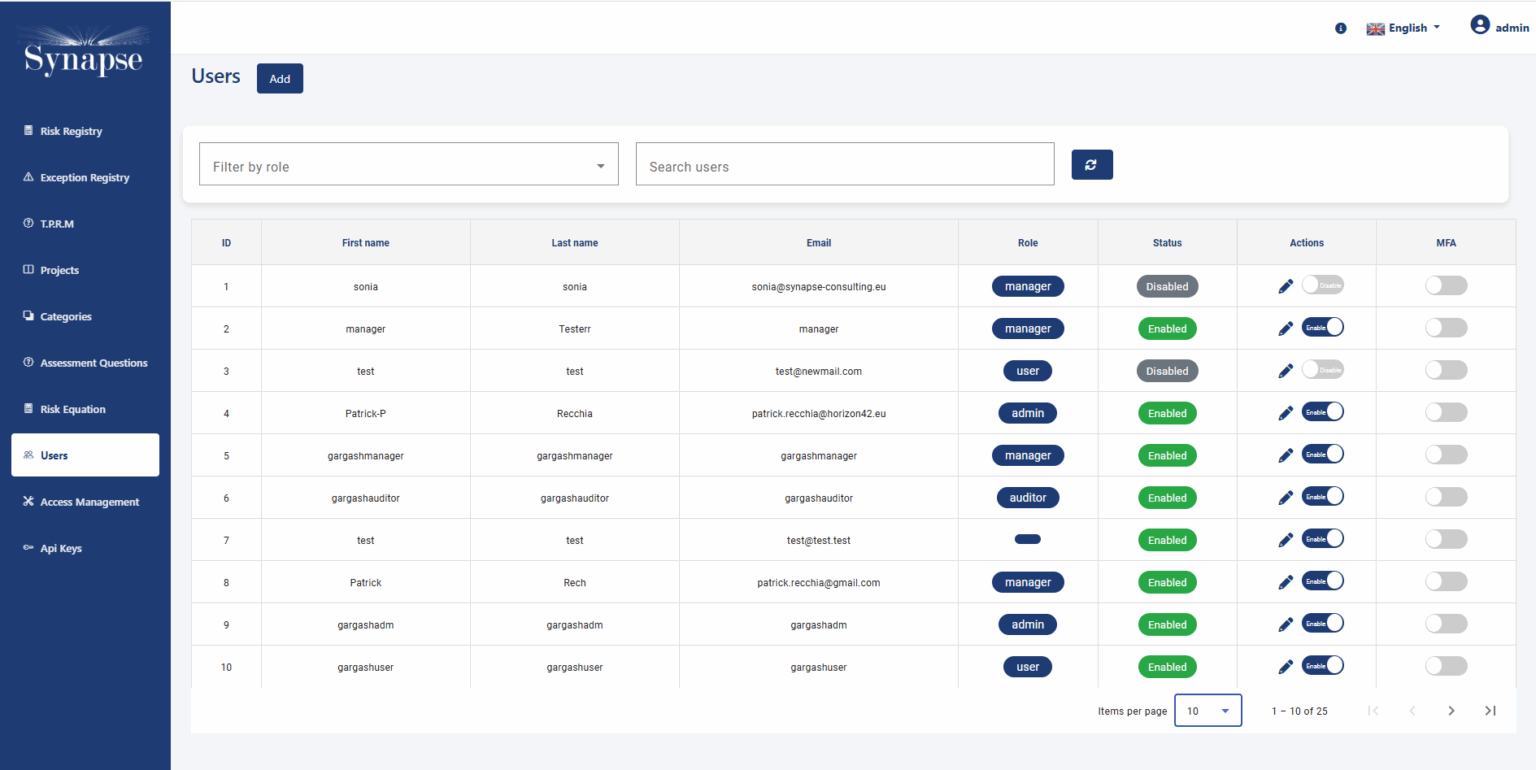
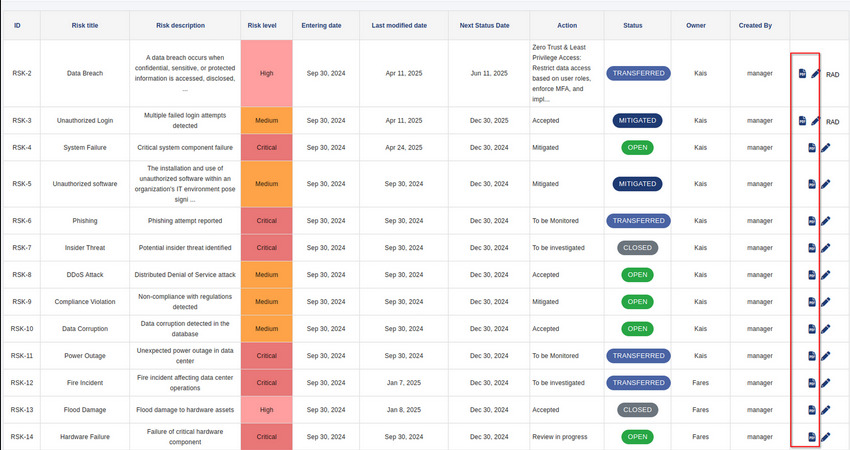
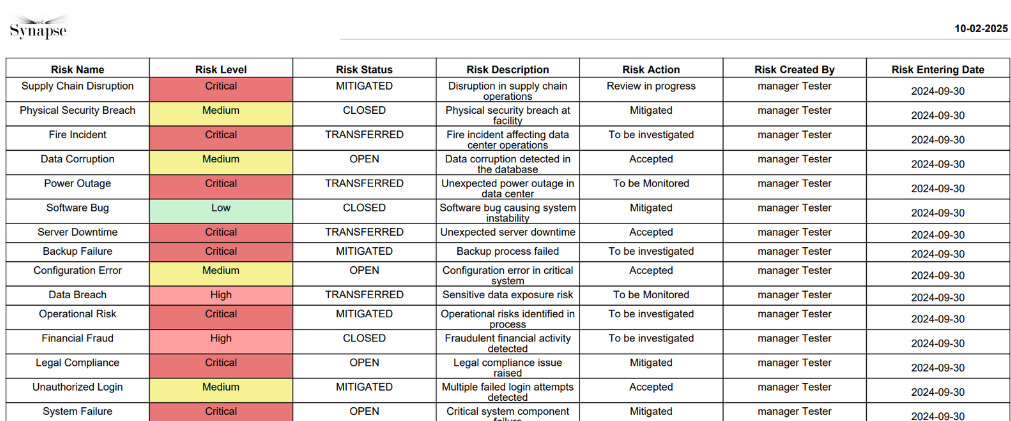
- Risk Registry
- Exception Registry
- Reporting
- support several Risk assessment framework out of the box
- Fully customized
- RBAC
- Auditor Role
- MFA supported
Risk Identification and Assessment:
Synapse-RM helps organizations identify and assess IT security risks across their internal systems and processes. The tool enables businesses to evaluate risks based on the likelihood of occurrence and the potential impact, helping them prioritize risk treatment efforts.
Third-Party Risk Management:
As part of its functionality, Synapse-RM includes tools for managing third-party risks, enabling organizations to evaluate and track the security and compliance of their external partners, vendors, and contractors.
This module ensures that organizations assess risks associated with third-party relationships to prevent security breaches originating from outside the company.
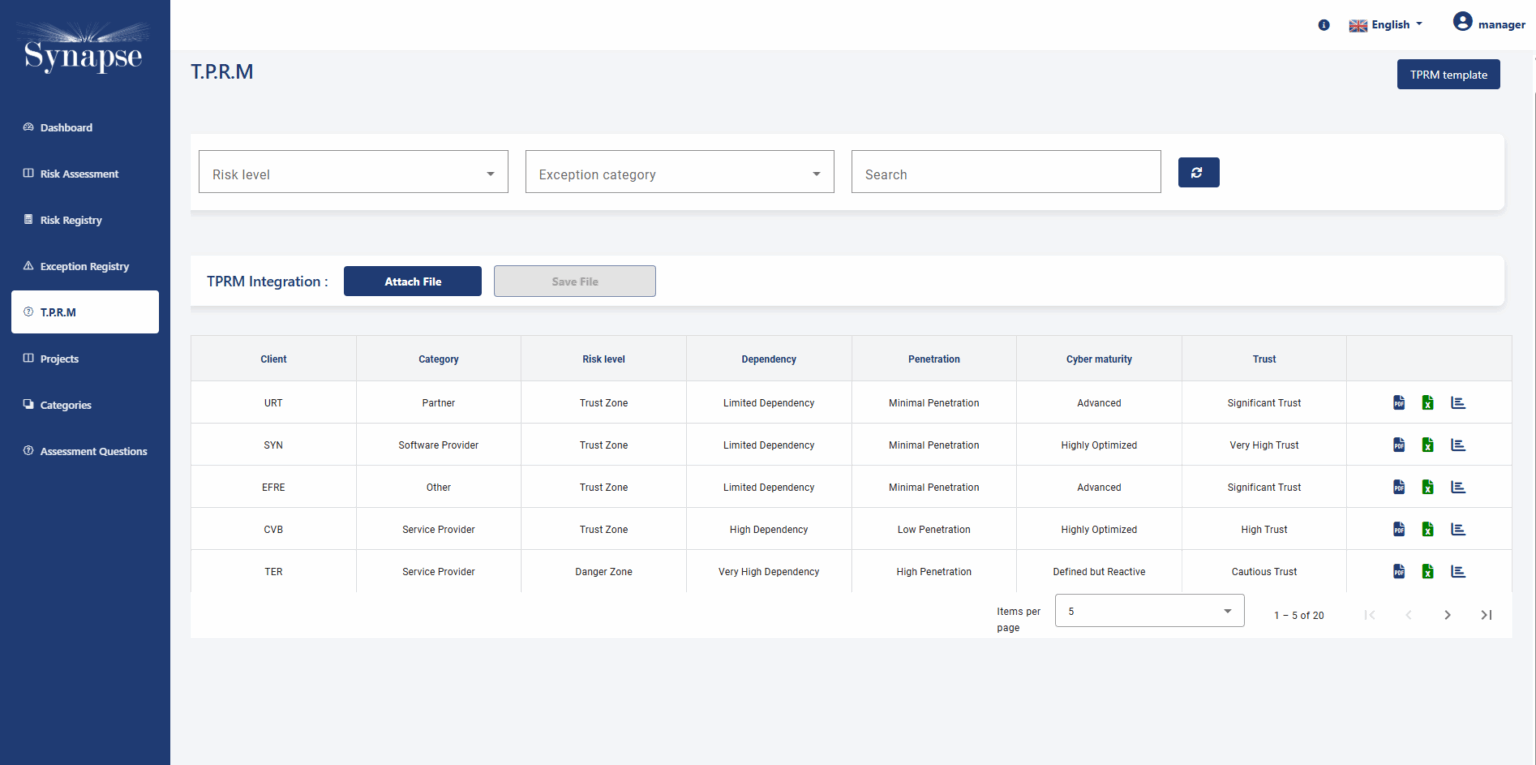
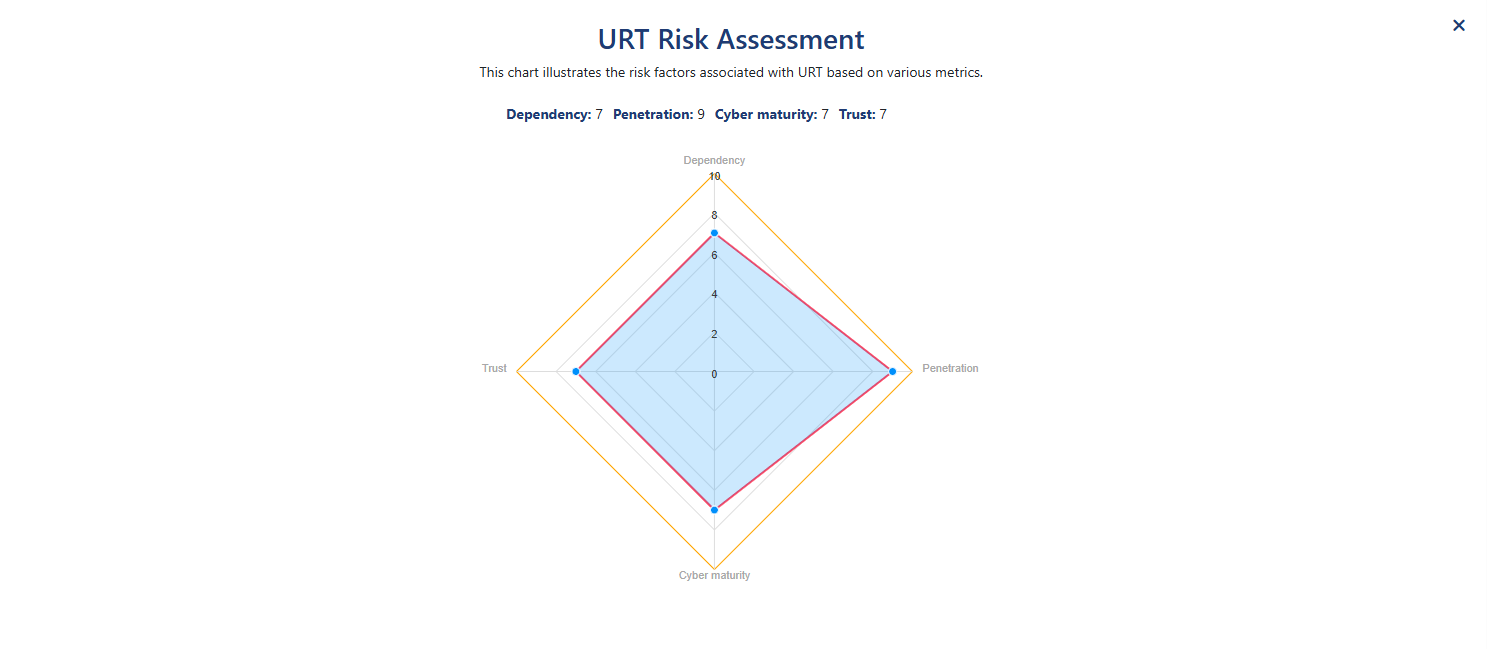
360° CISO Dashboard:
Synapse-RM provides a 360° view of the organization’s risk landscape through real-time dashboards, giving CISOs and security leaders a comprehensive view of both internal and third-party risks. These dashboards present key risk metrics, helping decision-makers stay on top of emerging threats, compliance gaps, and mitigation efforts.
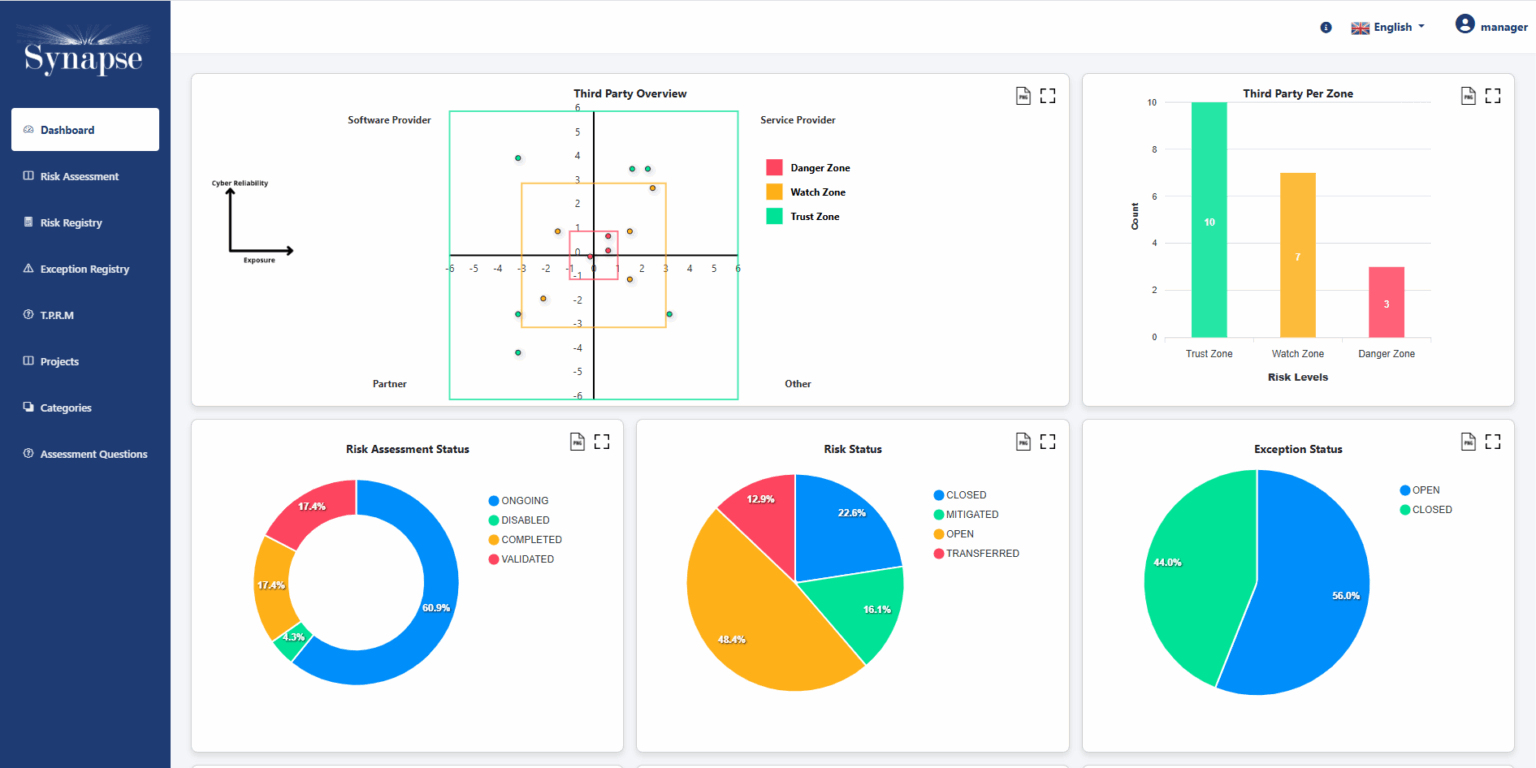
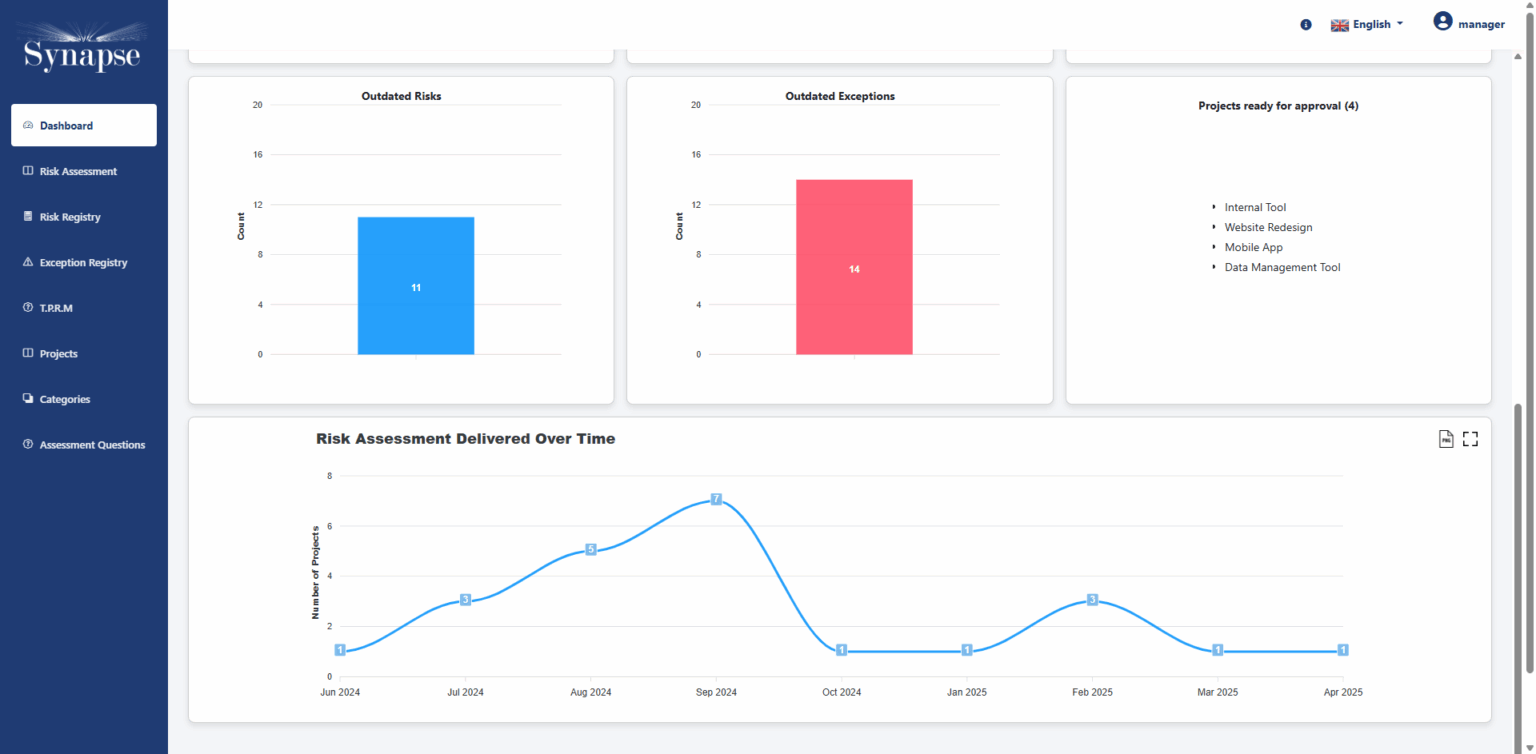
Comprehensive Reporting:
The tool generates detailed reports that help stakeholders and decision-makers understand risk trends, treatment strategies, and the effectiveness of mitigation actions. It also supports reporting for compliance, assisting organizations in demonstrating adherence to standards such as ISO 27001, NIST, and other relevant regulations.
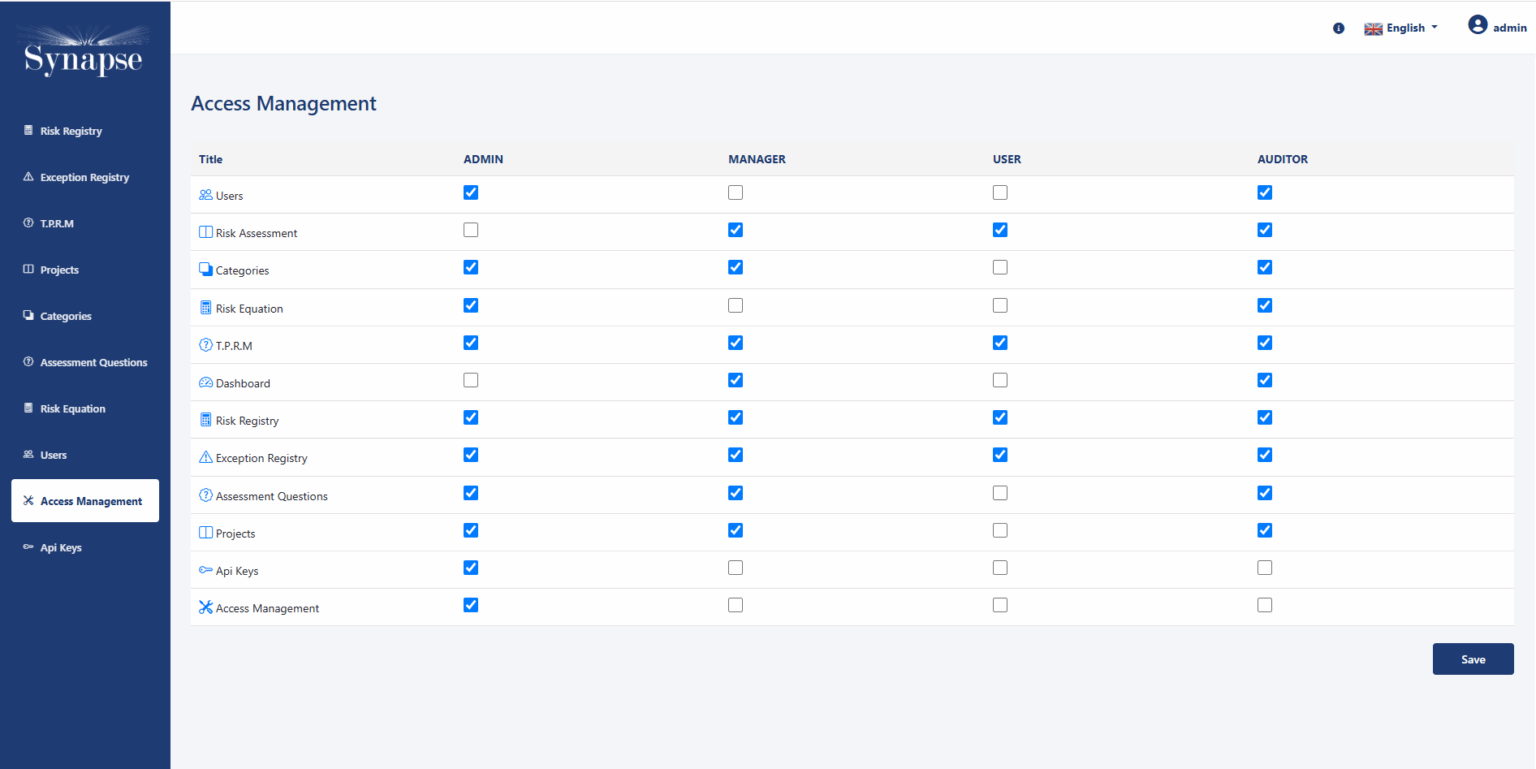
Role based Access Control:
Synapse-RM supports Role-Based Access Control (RBAC), ensuring that users only have access to the data and features that are relevant to their roles within the organization. This feature allows administrators to define specific roles and permissions, such as CISO, Risk Manager, Security Officer, Audito , etc., ensuring sensitive information is kept secure and accessible only to authorized personnel.